Imagine this: you're working on a project that requires you to access your devices remotely, but traditional methods just don’t cut it anymore. Well, AWS IoT SSH Tunnel is here to save the day. This powerful solution allows you to establish secure connections between devices and the cloud, giving you unparalleled control and flexibility. Whether you're managing IoT devices or troubleshooting from afar, this technology has got your back.
But let’s break it down a bit. AWS IoT SSH Tunnel isn’t just another buzzword in the tech world—it’s a game-changer. By leveraging the capabilities of AWS IoT, you can create secure tunnels that let you access your devices as if you were right there in person. This isn’t magic; it’s pure tech wizardry. And trust me, once you dive into this, you won’t want to go back to the old ways of doing things.
In today’s fast-paced digital landscape, security and efficiency are non-negotiable. That’s where AWS IoT SSH Tunnel shines. It’s not just about remote access; it’s about doing it securely, efficiently, and with minimal hassle. So, buckle up because we’re about to take you on a deep dive into the world of AWS IoT SSH Tunnel and how it can transform the way you work.
- Webster Hubbell The Inside Story Of A Legal Giant Who Made Waves
- Conan Obrien Family A Closer Look Into The Life Beyond The Latenight Spotlight
What Exactly is AWS IoT SSH Tunnel?
Let’s start with the basics. AWS IoT SSH Tunnel is a feature that enables secure, encrypted communication between your devices and the cloud. Think of it as a virtual corridor that lets you access your IoT devices remotely without exposing them to the dangers of the open internet. It’s all about creating a safe space for your data to flow back and forth.
Here’s how it works: when you set up an SSH tunnel through AWS IoT, you’re essentially creating a secure connection that allows you to interact with your devices as if they were on the same local network. This is achieved by using the Secure Shell (SSH) protocol, which encrypts all data transmitted between the device and the cloud.
Why Choose AWS IoT SSH Tunnel?
The choice is simple: AWS IoT SSH Tunnel offers a level of security and convenience that’s hard to beat. Here are a few reasons why it’s worth considering:
- Hugh Grants Children The Story Behind The Scenes
- Richard Pryor Comics The Legacy Of Laughter And Truth
- Security First: With encryption at its core, AWS IoT SSH Tunnel ensures that your data remains protected from prying eyes.
- Flexibility: Whether you’re managing a fleet of IoT devices or just need to troubleshoot one specific device, this solution adapts to your needs.
- Scalability: As your operations grow, AWS IoT SSH Tunnel can scale with you, handling more devices and connections without breaking a sweat.
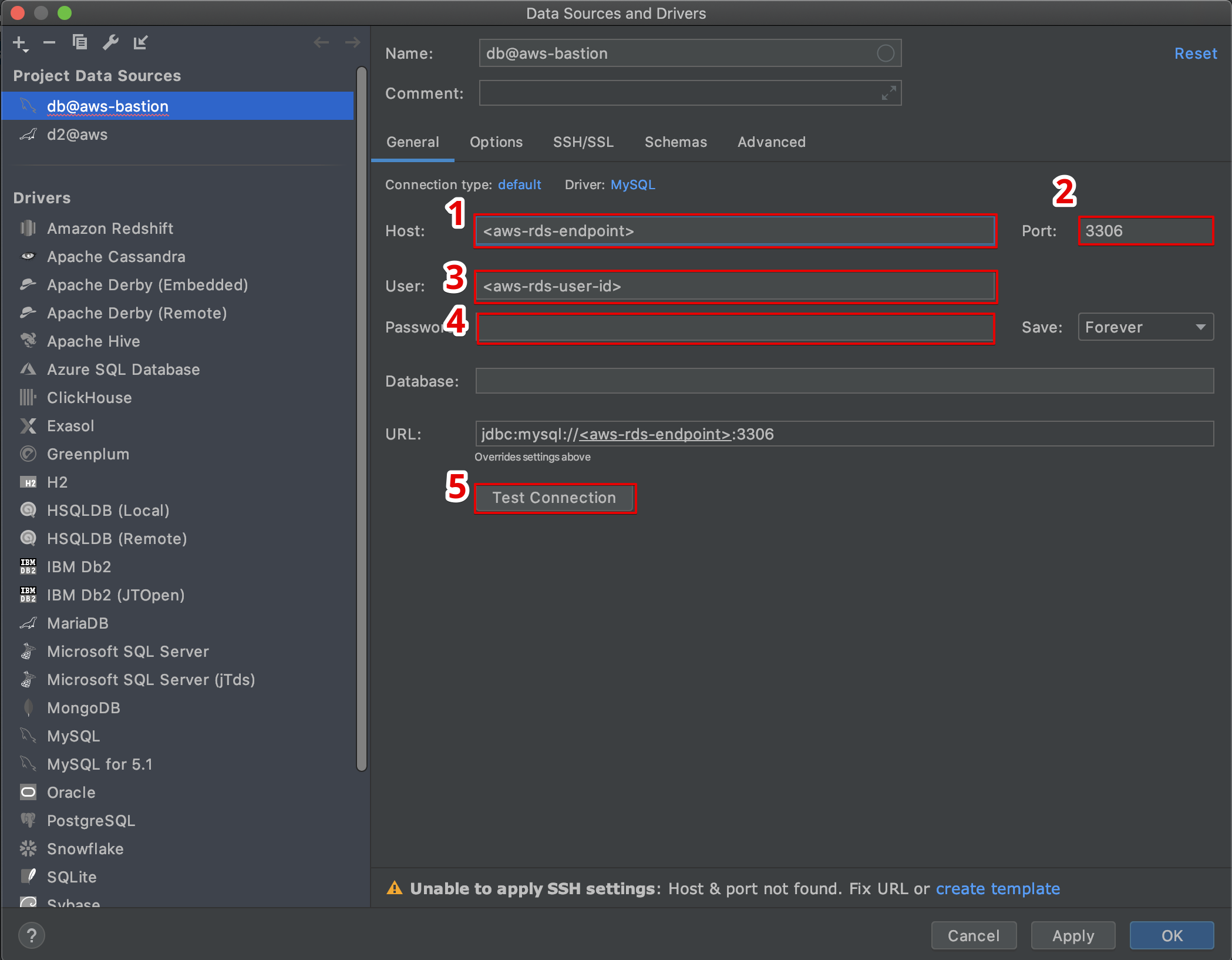
Setting Up AWS IoT SSH Tunnel: Step by Step
Now that you understand the basics, let’s talk about how to set it up. Don’t worry; it’s not as complicated as it sounds. Here’s a step-by-step guide to get you started:
First things first, you’ll need an AWS account. If you don’t have one yet, head over to the AWS website and sign up. Once you’re all set, follow these steps:
- Log in to your AWS Management Console and navigate to the AWS IoT Core service.
- Create a thing (a representation of your device in AWS IoT) and configure its settings.
- Set up the necessary policies and permissions to allow SSH access.
- Install the AWS IoT Device SDK on your device and configure it to connect to AWS IoT.
- Finally, establish the SSH tunnel using the AWS IoT SSH feature.
And voila! You’re ready to start accessing your devices remotely with ease.
Troubleshooting Common Issues
Even the best-laid plans can hit a snag. If you encounter any issues while setting up your AWS IoT SSH Tunnel, here are a few troubleshooting tips:
- Check your device’s network connectivity to ensure it’s properly connected to the internet.
- Verify that the necessary permissions and policies are correctly configured in AWS IoT Core.
- Make sure the AWS IoT Device SDK is installed and configured correctly on your device.
Remember, patience is key. If something doesn’t work the first time, don’t give up. Keep tweaking until you get it right.
Security Features of AWS IoT SSH Tunnel
Security is a top priority when it comes to remote access, and AWS IoT SSH Tunnel doesn’t disappoint. Here’s a closer look at some of its key security features:
First off, the tunnel itself is encrypted using the SSH protocol, which ensures that all data transmitted between your device and the cloud is secure. Additionally, AWS IoT Core provides robust authentication and authorization mechanisms to ensure that only authorized users can access your devices.
But that’s not all. AWS also offers features like device shadowing and message filtering, which add an extra layer of security and control to your IoT setup. These features allow you to monitor and manage your devices more effectively, reducing the risk of unauthorized access or data breaches.
Best Practices for Secure Remote Access
To get the most out of AWS IoT SSH Tunnel, it’s important to follow some best practices:
- Always use strong passwords and consider implementing multi-factor authentication (MFA) for added security.
- Regularly update your devices and the AWS IoT Device SDK to ensure you have the latest security patches.
- Monitor your device activity closely and set up alerts for any suspicious behavior.
By following these guidelines, you can help ensure that your AWS IoT SSH Tunnel remains secure and reliable.
Use Cases for AWS IoT SSH Tunnel
So, where can you use AWS IoT SSH Tunnel? The possibilities are endless. Here are a few examples:
- Remote Device Management: Use AWS IoT SSH Tunnel to manage and configure your IoT devices from anywhere in the world.
- Troubleshooting: Quickly diagnose and fix issues with your devices without needing to be physically present.
- Software Updates: Push software updates to your devices securely and efficiently.
No matter what your specific needs are, AWS IoT SSH Tunnel can help you achieve them with ease.
Real-World Examples
Let’s take a look at some real-world examples of how companies are using AWS IoT SSH Tunnel:
One company used AWS IoT SSH Tunnel to manage a fleet of remote sensors used for environmental monitoring. By leveraging the secure tunnel, they were able to collect data and make adjustments to their sensors without needing to send technicians to the field.
Another organization used the technology to troubleshoot issues with their smart home devices. With AWS IoT SSH Tunnel, they were able to quickly identify and resolve problems, improving the overall user experience.
Cost Considerations
Now, let’s talk about the elephant in the room: cost. AWS IoT SSH Tunnel is part of the broader AWS IoT Core service, which operates on a pay-as-you-go model. This means you only pay for what you use, making it a cost-effective solution for businesses of all sizes.
Additionally, AWS offers a free tier that includes a certain amount of usage for free, allowing you to test and experiment with the service before committing to a larger deployment.
Maximizing Your Budget
To get the most out of your budget, consider the following tips:
- Start small and scale up as needed. This allows you to test the waters without incurring significant costs.
- Monitor your usage closely and adjust your deployment accordingly to avoid unnecessary expenses.
By being mindful of your usage and planning ahead, you can keep costs under control while still reaping the benefits of AWS IoT SSH Tunnel.
Future Trends in IoT and SSH Tunneling
As technology continues to evolve, so too will the capabilities of AWS IoT SSH Tunnel. Here are a few trends to watch for in the near future:
- Increased Automation: Expect to see more automation in the setup and management of SSH tunnels, reducing the need for manual intervention.
- Enhanced Security Features: With cyber threats becoming more sophisticated, AWS will likely continue to enhance the security features of its IoT services.
- Broader Integration: AWS IoT SSH Tunnel will likely become more integrated with other AWS services, offering even more powerful capabilities.
Stay tuned for these exciting developments and be ready to embrace the future of IoT and SSH tunneling.
Staying Ahead of the Curve
To stay ahead of the curve, it’s important to keep learning and adapting. Follow industry news and updates from AWS to ensure you’re always up to speed with the latest trends and technologies.
Conclusion
In conclusion, AWS IoT SSH Tunnel is a powerful tool that can revolutionize the way you work with IoT devices. By providing secure, efficient remote access, it offers a level of flexibility and control that’s hard to match. Whether you’re managing a fleet of devices or just need to troubleshoot one specific issue, this technology has got you covered.
So, what are you waiting for? Dive into the world of AWS IoT SSH Tunnel and see how it can transform your operations. And don’t forget to share your thoughts and experiences in the comments below. We’d love to hear from you!
Table of Contents
- What Exactly is AWS IoT SSH Tunnel?
- Why Choose AWS IoT SSH Tunnel?
- Setting Up AWS IoT SSH Tunnel: Step by Step
- Troubleshooting Common Issues
- Security Features of AWS IoT SSH Tunnel
- Best Practices for Secure Remote Access
- Use Cases for AWS IoT SSH Tunnel
- Real-World Examples
- Cost Considerations
- Future Trends in IoT and SSH Tunneling


Detail Author:
- Name : Miss Piper Pagac DDS
- Username : ogorczany
- Email : kyle.littel@ratke.net
- Birthdate : 1998-07-05
- Address : 7426 Kirlin Court Cindychester, OK 68904-2537
- Phone : +17145319342
- Company : West PLC
- Job : Artillery Officer
- Bio : Non aperiam quia repellendus eligendi. Quidem sed qui rem aut repudiandae. Debitis perspiciatis atque minima qui maiores. Dolor doloremque quo velit provident ad provident sed temporibus.
Socials
instagram:
- url : https://instagram.com/rubye_welch
- username : rubye_welch
- bio : Animi veritatis distinctio non rerum provident quis. Quod quia explicabo quia ut quam.
- followers : 3820
- following : 2425
facebook:
- url : https://facebook.com/rubyewelch
- username : rubyewelch
- bio : Quaerat ipsa voluptatem quod ut.
- followers : 4313
- following : 1886