So, you're looking to securely connect your remote IoT VPC on AWS, huh? Let’s be real—IoT security is one of the hottest topics these days, and for good reason. As more devices get connected to the cloud, the risks of unauthorized access and data breaches skyrocket. If you’re diving into AWS VPC for your IoT setup, you’re already on the right track. But the real question is: Are you doing it right? Let’s break it down for you.
Whether you’re a seasoned cloud architect or just starting out, setting up a secure IoT VPC on AWS can feel like solving a Rubik’s Cube—complex but solvable with the right approach. This guide isn’t just about theory; it’s about practical steps to ensure your IoT devices are as secure as Fort Knox. From configuring VPC settings to implementing best practices, we’ve got you covered.
Now, before we dive deep into the technical details, let’s address the elephant in the room: Why does this matter? Think about it—your IoT devices are collecting sensitive data, and if someone hacks into your network, it’s game over. This isn’t just about protecting your devices; it’s about safeguarding your business and your customers. So, buckle up because we’re about to take you on a journey to fortify your AWS IoT VPC setup.
- Fred Gwynne Movies And Tv Shows The Iconic Journey Of A Legendary Actor
- Laci Peterson The Untold Story That Keeps Us Guessing
Understanding the Basics of AWS VPC and IoT
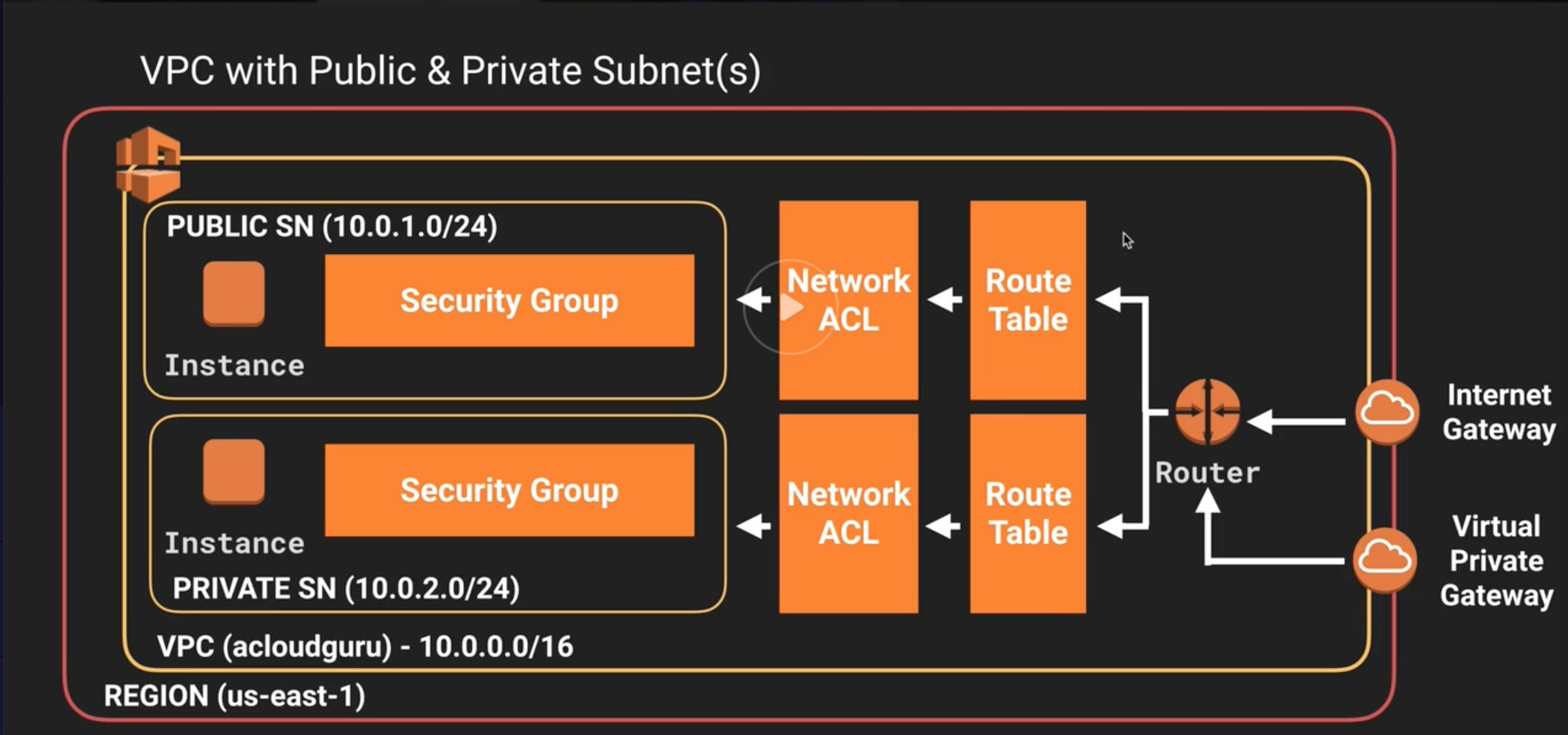
Let’s start with the basics. AWS VPC (Virtual Private Cloud) is essentially your own private network within AWS. It’s like having your own little corner of the internet where you can control everything—from IP addresses to security groups. When it comes to IoT, this becomes crucial because you need a secure environment to manage all those connected devices.
Here’s a quick rundown of what AWS VPC offers:
- Customizable IP Address Ranges: You can define your own IP ranges, which gives you more control over how devices communicate.
- Subnet Management: Split your network into smaller segments to improve security and performance.
- Security Groups and Network ACLs: These are like firewalls that control inbound and outbound traffic to your instances.
- Private and Public Subnets: Keep sensitive data isolated in private subnets while allowing public access where needed.
For IoT, this setup is gold. Imagine having thousands of devices sending data to your cloud. Without proper VPC configuration, it’s like leaving your front door wide open. But with AWS VPC, you can lock it down tight.
- Renee Zellweger A Journey Through Stardom And Timeless Talent
- Ultimate Break Your Ultimate Guide To Recharging And Relaxing
Why Securely Connecting IoT Devices Matters
Now, let’s talk about why securing your IoT devices is a big deal. According to a report by Gartner, the number of IoT devices is expected to reach over 25 billion by 2030. That’s a lot of devices, and each one is a potential entry point for hackers. If you’re not careful, your IoT setup could become a playground for cybercriminals.
Here are some stats to make you sit up and take notice:
- Over 70% of IoT devices have significant security vulnerabilities.
- In 2022 alone, there were over 1.5 billion IoT-related cyberattacks globally.
- A single compromised IoT device can lead to a massive data breach, costing businesses millions of dollars.
So, if you’re managing an IoT fleet on AWS, securing your VPC is not optional—it’s a necessity. Let’s move on to the next section to see how you can achieve this.
Setting Up Your AWS IoT VPC
Alright, let’s get our hands dirty. Setting up your AWS IoT VPC involves a few key steps. First, you’ll need to create a VPC in the AWS Management Console. Once that’s done, you can start configuring your subnets, security groups, and routing tables.
Step 1: Create Your VPC
Head over to the AWS Management Console and navigate to the VPC dashboard. Click on “Create VPC” and define your IP address range. For most IoT setups, a /16 CIDR block should suffice. Once your VPC is created, you can start adding subnets.
Step 2: Configure Subnets
Subnets are like smaller networks within your VPC. You’ll want to create both public and private subnets. Public subnets will allow internet access, while private subnets will keep your sensitive data isolated.
Here’s a quick checklist:
- Create at least two public subnets for redundancy.
- Create private subnets for devices that don’t need internet access.
- Enable DNS resolution to allow communication between subnets.
Implementing Security Best Practices
Now that your VPC is set up, it’s time to lock it down. Security best practices are your first line of defense against cyber threats. Here are some tips to keep your IoT VPC secure:
Use Security Groups Wisely
Security groups act as virtual firewalls for your instances. Make sure you only allow necessary traffic and restrict access to sensitive ports. For example, if your IoT devices only need to communicate with your backend servers, block all other traffic.
Enable Network ACLs
Network ACLs (Access Control Lists) provide an additional layer of security by controlling traffic at the subnet level. Use them to whitelist trusted IP addresses and block suspicious activity.
Monitor Traffic with CloudWatch
AWS CloudWatch is your best friend when it comes to monitoring your VPC. Set up alarms for unusual activity, such as unexpected traffic spikes or unauthorized access attempts. This way, you can catch potential threats before they become serious issues.
Managing IoT Device Access
IoT devices are unique in that they often have limited computational power and memory. This makes them more vulnerable to attacks. To secure your IoT devices, you’ll need to manage their access carefully.
Use IAM Roles
AWS IAM (Identity and Access Management) allows you to define roles with specific permissions. Assign roles to your IoT devices based on their needs. For example, a device that only sends data to a backend server doesn’t need access to other resources.
Implement Device Authentication
Device authentication ensures that only authorized devices can connect to your VPC. Use AWS IoT Core’s built-in authentication features, such as X.509 certificates, to verify device identities.
Encrypting IoT Data in Transit
Data encryption is a must for any IoT setup. Whether your data is traveling between devices or being stored in the cloud, it needs to be protected. AWS offers several encryption options to keep your data safe.
Use TLS for Secure Communication
Transport Layer Security (TLS) encrypts data as it travels between devices and your VPC. AWS IoT Core supports TLS 1.2, which is currently the most secure version. Make sure all your devices are configured to use TLS for communication.
Leverage KMS for Encryption Keys
AWS Key Management Service (KMS) lets you manage encryption keys for your data. Use KMS to generate and store keys securely, and rotate them regularly to minimize the risk of compromise.
Monitoring and Auditing Your IoT VPC
Even the best security measures can fail if you’re not monitoring your VPC regularly. AWS provides several tools to help you keep an eye on your IoT setup.
Use AWS CloudTrail for Auditing
CloudTrail logs all API calls made to your AWS resources, including your VPC. Review these logs regularly to detect any suspicious activity. You can also set up alerts for specific events, such as changes to security groups or IAM roles.
Enable VPC Flow Logs
VPC Flow Logs capture information about IP traffic going in and out of your VPC. Use this data to identify traffic patterns and detect potential threats. Combine flow logs with CloudWatch for real-time monitoring.
Troubleshooting Common Issues
No matter how careful you are, issues can still arise. Here are some common problems you might encounter when setting up your IoT VPC and how to fix them:
Device Connectivity Issues
If your IoT devices can’t connect to your VPC, check the following:
- Ensure your security groups allow the necessary traffic.
- Verify that your devices are using the correct IP addresses and ports.
- Check your routing tables to ensure traffic is being routed correctly.
Performance Bottlenecks
If your IoT devices are experiencing performance issues, consider the following:
- Optimize your subnets to reduce latency.
- Use AWS Direct Connect for faster and more reliable connections.
- Monitor your VPC resources to identify and resolve bottlenecks.
Future-Proofing Your IoT VPC
Technology is always evolving, and so are the threats. To keep your IoT VPC secure in the long run, you’ll need to stay ahead of the curve. Here are some tips for future-proofing your setup:
Stay Updated with AWS Best Practices
AWS regularly updates its best practices for VPC and IoT security. Make it a habit to review these updates and implement them in your setup.
Invest in Automation
Automation can help you manage your IoT VPC more efficiently. Use AWS Lambda functions to automate tasks like monitoring, logging, and alerting. This way, you can focus on more strategic activities.
Conclusion
Securing your remote IoT VPC on AWS is a complex but essential task. By following the steps outlined in this guide, you can create a robust and secure environment for your IoT devices. Remember, security is an ongoing process, so stay vigilant and keep learning.
Now, it’s your turn. Have you implemented any of these strategies in your IoT setup? Share your experiences in the comments below. And if you found this guide helpful, don’t forget to share it with your network. Together, we can make the IoT world a safer place.
Table of Contents
- Understanding the Basics of AWS VPC and IoT
- Why Securely Connecting IoT Devices Matters
- Setting Up Your AWS IoT VPC
- Implementing Security Best Practices
- Managing IoT Device Access
- Encrypting IoT Data in Transit
- Monitoring and Auditing Your IoT VPC
- Troubleshooting Common Issues
- Future-Proofing Your IoT VPC
- Conclusion


Detail Author:
- Name : Phyllis Halvorson III
- Username : bartoletti.hayley
- Email : lueilwitz.janice@bergstrom.biz
- Birthdate : 1985-12-09
- Address : 818 Idell Ports Apt. 893 Davisfurt, NV 20780
- Phone : +1.680.345.1114
- Company : Murphy and Sons
- Job : Fast Food Cook
- Bio : Omnis alias sint explicabo ab consequatur voluptas non. Eum molestiae numquam aut. Rerum facere ut quas fugit dignissimos.
Socials
instagram:
- url : https://instagram.com/janelle_cremin
- username : janelle_cremin
- bio : Et aut libero ea sed aliquam est. Aut vel nisi magni eligendi. In id voluptas corrupti at.
- followers : 6892
- following : 1658
facebook:
- url : https://facebook.com/jcremin
- username : jcremin
- bio : Deserunt consequatur et natus necessitatibus quisquam illo fugit.
- followers : 183
- following : 2231
twitter:
- url : https://twitter.com/janelle_cremin
- username : janelle_cremin
- bio : Eum sit vel labore beatae tenetur. Inventore id vero voluptate ea voluptas voluptatem. Quam odio numquam ad ea quia id molestias enim.
- followers : 843
- following : 2840